
In 2017, ransomware cyberattacks became a serious, recurring threat for businesses, especially in the healthcare industry. Cybercriminals are getting smarter and more sophisticated, and the margin for human error is increasing.
As 2018 begins, what can we do to combat this threat? To defeat this enemy, we must know the enemy.
In this report, we are going to break down the anatomy of a ransomware attack, the ransomware trends we saw in 2017, and what we believe the ransomware trend forecast will be in 2018.
The Anatomy of a Ransomware Attack
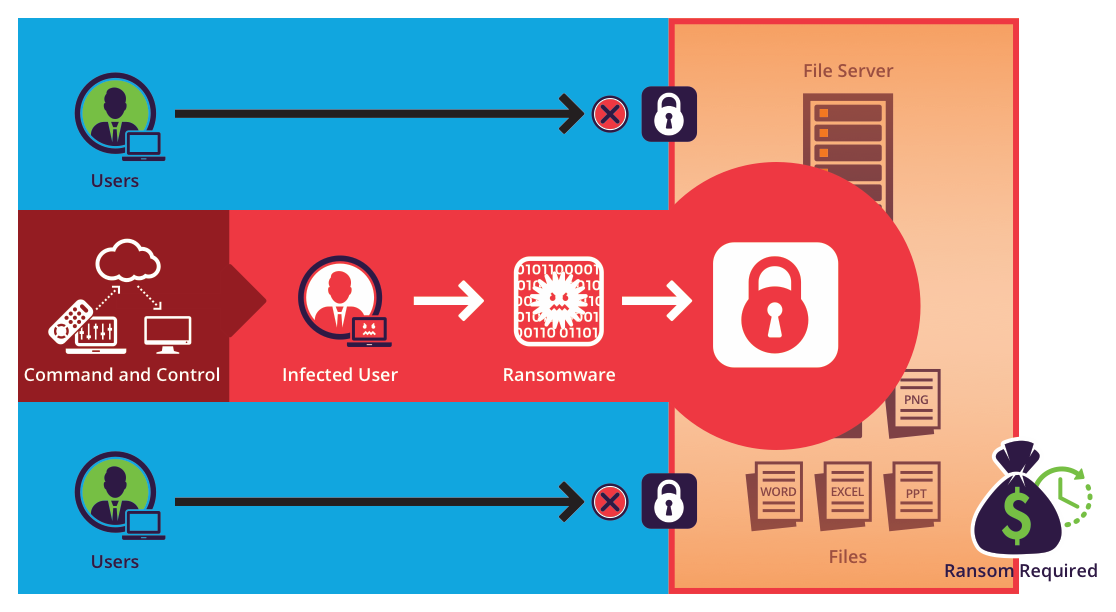
Why is ransomware so effective?
Ransomware is when an intruder gains access to your computer, encrypts important files with a private key, and demands a ransom to decrypt the information.
Email is the number one attack vector for ransomware (otherwise known as phishing), but ransomware comes in many shapes and sizes.
People continually fall victim to ransomware attacks because of human error like our susceptibility and The Overconfidence Dilemma.
There are other ways for ransomware to affect software, such as network servers, but email remains as the top three causes of this kind of data breach.
Furthermore, as we saw from the June 2017 Ukraine cyberattacks, ransomware’s reach is worldwide. Soon after Ukraine’s attacks, similar Petya malware infections were reported in France, Germany, Italy, Poland, Russia, United Kingdom, the United States and Australia.
The international infection prompted the Ukrainian government to make an official announcement stating that the attacks had been halted. This event raised ransomware’s threat level to a worldwide epidemic.
When ransomware strikes
Modern ransomware no longer needs to write itself into a disk to take effect. Today’s ransomware attacks execute in memory and do their work in memory.
Even if you disallow your users to install programs onto our Windows computer, you can still fall victim to other hacking tools. For example, hackers can execute advanced phishing campaigns using LinkedIn.
What to do after a ransomware attack
If you are infected by ransomware, you have three options (or sometimes four):
- You can get rid of your infected computers
- You can restore from a backup
- If you don’t have backups, then you pay the amount on the ransom note
- Or if you automate everything, you can rebuild everything from scripts. (This is a possible solution, but it is a lot more work to do.)
Sometimes, after you pay the ransom payments, the cybercriminals will give you a decryption key to get your data back. Other times, they won’t.
Sometimes, they’ll even return to hit you again the following week. Ransomware attacks can be unpredictable.
Ransomware Trends in 2017

Email breaches are increasing
According to Statista, roughly 269 billion emails were sent and received each day in 2017. As a result, it comes as no surprise that email is a preferred target for cybercriminals.
The threat of email breaches has risen considerably from 2016 to 2017. In fact, email was the biggest source of data breaches in 2017, with 73 breaches occurring between Jan. 1 and the end of November reported to HHS, affecting 573,698 people.
Ransomware doesn’t only affect those in healthcare. It can virtually affect any industry, such as when Uber allegedly paid a $100,000 ransom to hackers and Spanish telecoms giant Telefonica paid hackers $550,000 in Bitcoin.
But healthcare is especially targeted with more than 4,000 new ransomware attacks daily due to the black market value of protected health information (PHI) transmitted every day.
For instance, on August 28, 2017, the Lukitus Campaign sent out 23 million emails in 24 hours. Researchers determined that the emails sent out in the attack were “extremely vague,” with subjects lines such as “please print,” “documents,” “images,” “photos,” “pictures,” and “scans” to convince victims into infecting themselves with Locky ransomware.
The recurrence of ransomware led the HHS to release a guidance on ransomware in 2016. In 2017, the HHS had to reiterate the OCR Ransomware Guidance following more recent attacks such as the WannaCry attack.
As a result, it should come as no surprise that ransomware in the form of email breaches will continue to multiply in 2018.
HIPAA fines are rising
According to the HHS, “The HIPAA Security Rule requires implementation of security measures that can help prevent the introduction of malware, including ransomware.” Failure to do so constitutes a HIPAA violation, which is closely followed by a fine.
Anthem paid a $115 million fine for a single breach that happened in 2015, which earned a record for the largest fine ever issued by the HHS.
But the costly fine was appropriate, considering the breach affected 80 million Americans in 2015. PHI like social security numbers, birth dates, health conditions, and more were breached.
In contrast, 2016’s total HIPAA fines amounted to $23 million.
One fine alone in 2017 equaled five times more than the total amount of fines in 2016.
With the surplus of ransomware attacks due to insufficient security and staff training, we expect these fines to increase.
Ransomware payments are decreasing

In 2016, 48% of every organization in the United States had either been breached or suffered a kind of ransomware attack – that they know about.
But while ransomware attacks have increased, the amount of payment demanded per breach has dramatically decreased.
For example, in 2016, Hollywood Presbyterian Medical Center paid a $17,000 ransom in bitcoin to a hacker when their computers were hacked on Feb 5.
Now, with recent ransomware variants such as WannaCry ransomware and Bad Rabbit, the ransom price has gone down to an average cost of $544, according to Symantec’s Ransomware 2017 report.
With the threat of effective ransomware like WannaCry and Petya, one would think that the cost would drastically increase. However, we believe cybercriminals are operating with the mindset of charging a ransom that most people would pay, but hitting more people to extract more money.
This immoral business model seems to be the most profitable for cybercriminals. In 2016, ransomware cybercriminals took in about $1 billion last year based on money coming into ransomware-related Bitcoin wallets.
Ransomware will continue to grow over the next few years
The Cisco 2017 Annual Cybersecurity Report believes ransomware will be growing at a yearly rate of 350%.
The 2016 Cybercrime Report from Cybersecurity Ventures predicts cybercrime will cost the world in excess of $6 trillion annually by 2021, making it more profitable than the global trade of all major illegal drugs combined.
Due to the amount of ransomware attacks in U.S. healthcare, the HHS has issued a new stance in ransomware. Whether you pay the ransom or not, or restore from backup, or destroy the machine, the HHS defines the ransomware as a breach that must be reported.
Back in 1999, ransomware was spread through malware such as viruses.
Today, in 2018, cybercriminals have become more sophisticated and sneakier.
These criminals utilize macros in email attachments for office documents to release their ransomware. (Remember the Google Doc phishing scam that happened back in May 2017?)
Ransomware thrives on human error

A 2017 study from the University of Texas at San Antonio, titled “The Overconfidence Dilemma”, found that the average internet user’s ability to detect scams is believed to be a lot higher than it actually is.
For instance, the average internet user still thinks all the threats are from Nigerian princes with bad spelling.
Unfortunately, that’s not the case anymore.
As we saw with the Google Doc phishing scam, there were no obvious spelling or grammar errors, the logo was convincing, and the HTML was well done. Most untrained eyes would believe they opened a legitimate email.
Macro use in modern businesses
In a Microsoft Office document, you can embed a macro to automate certain tasks for you. For example, you can add a pre-designed table to a Word document, or add a sophisticated calculation to an Excel sheet.
As handy as macros can be, cybercriminals were quick to exploit it, launching a series of macro malware to unsuspecting consumers.
Hackers adopted macros and embedded powershell job script demands to make the infected computer perform certain tasks. There are even more advanced threats out there that hack the computer from PDF documents.
In the early 2000s, security researchers saw a trend where executables were being delivered via email. As a result, the Internet blocked executables. This has continued to happen to this day.
Soon, we believe that a discussion will arise about whether the same is true for macros. Will they eventually become obsolete, like their predecessor executables?
Macros, especially in Excel documents, have a useful business purpose to them. As a result, businesses are more reluctant to give them up.
While that is understandable, at Paubox, we believe that macros are bad for email because the security risks outweigh the benefits.
Anti-Viruses battle against ransomware

Symantec, Norton, McAfee – we all know the big antivirus security firms. But how does antivirus software work?
Typically, an antivirus software will have a file with several hashes in them. Hashing is the transformation of a string of characters into a shorter fixed-length value or key that represents the original string. This is done to index and retrieve items in a database faster.
Each hash in antivirus software identifies a signature that each known virus or ransomware displays.
In the past, you would have this software installed on your computer or network server. Every 30 minutes or an hour, the software would run and check for any signatures or new threats.
If a new signature is found, the software takes the signature and distributes it to workstations or downloads it to a workstation.
You can amplify your antivirus software to check your large files as well, doing it as often as every minute to protect every machine against ransomware. However, this puts a significant load on the antivirus vendor.
The average lifetime of a ransomware signature, such as Cerber, is gone in 15 seconds.
99% of all ransomware on the internet changes its hash before one minute is up.
Even if your antivirus software could check every minute, you would still be two seconds too late.
And if you are too late and subsequently infected, it would take 33 employee hours to recover from a ransomware attack.
This is why ransomware is working. There’s a new threat level landscape, and the old income players have not adapted quick enough to take advantage of the new information out there.
How do we stop ransomware?

Start building data sets
If you are using software, odds are you are in the Cloud using AWS, Azure, or Google as your vendor. These cloud vendors often provide machine learning and AI so you don’t need to reinvent the wheel.
What you do need are data sets.
In email encryption, we need data sets that distinguish the good macros from the bad macros. Over time, if you build a big enough data set, you can get predictable, sharp results so that you don’t have to rely on signatures that don’t keep up with the modern attack vector.
Look at domain ages
Another way to protect against Ransomware attacks is with something we built into Paubox. We call it “Domain Age”.
For example, if you receive an email or a link in an email to a domain name that has been around for 10 days, the link or email is most likely not legitimate.
For every link and email address domain that is sent to our customers, Paubox’s spam filtering checks to see if the link or email has been around for a sufficient amount of time. If not, we determine that the email is bogus with bad intentions and prevent it from delivering to the inbox.
This security check is important considering how easy it is to register domain names these days. You can even register domain names with scripts.
You can also buy 50 domain names in 10 minutes. What legitimate purpose is there to need that many domain names? We don’t think there’s any, yet it is still allowed.
We think there should be a lot more verification in place when purchasing a domain name. For example, there is nothing stopping you from buying “wellsfargoincalifornia.com” or “wellsfargoinnortherncalifornia.org”, or simply replacing an “e” with a “3”, and so on.
Host phishing competitions
Phishing competitions are good exercise for large companies.
Simply launch a minor phishing attack to determine who the gullible users in your company are.
Alternatively, your IT team can try and phish the CTO to see if your director of security experts can be fooled.
Not only is this a good team building exercise, but it can improve user education for your staff.
Ransomware Trend Forecast for 2018

With all this in mind, these are the three we believe will continue to prevail in 2018.
Email remains top dog
We believe email will remain the top dog for the attack vectors of ransomware.
Why? Because email is still the weakest link, and cybercriminals are getting smarter.
We’ve seen cybercriminals target high-profile figures, such as when the personal Gmail account of John Podesta, a former White House chief of staff and the chairman of Hillary Clinton’s 2016 U.S. presidential campaign, was compromised in a data breach.
He thought he had received a password change request from Gmail on his iPhone, but in reality, he fell victim to a spear-phishing attack launched by the hacking group Fancy Bear (who were allegedly affiliated with Russian intelligence services).
Podesta complied with the phishing email and changed his password at 4AM. This gave the hacking group direct access to his personal Gmail account.
Podesta’s email data breach is a perfect example of human error. After all, who is paying attention at 4 in the morning?
Portals continue to suck
From an email encryption standpoint, portals will continue to suck.
At Paubox, we built our solution to get rid of portals. We deliver the email encrypted, straight to the inbox, without any friction. This is because we believe user experience for email encryption is just as important as the military grade security.
In 2017, we learned that 79% of people use their smartphone to read emails. But retrieving an email from a portal on a mobile device is even worse than trying to access an email in a portal on your desktop.
Ultimately, portals are not the way to go. People don’t want to deal with portals on a small screen because the user interface is terrible.
“Don’t make me login to one more portal. Please.” – An actual quote we’ve heard from a portal user.
Ample market opportunity
We believe there is ample market opportunity in encrypted email and the encrypted security space.
We know healthcare needs help safeguarding their information from all sorts of prying eyes – whether it be protection from a cybercriminal or a disgruntled former employee.
Ransomware is a worldwide epidemic with security teams constantly looking out for new infections. As such, organizations – especially in healthcare – need to get ahead of ransomware to reduce its threat.
With a strong email encryption solution like Paubox, you can do just that. Not only is Paubox the easiest way to send and receive HIPAA compliant email, it also includes robust SPAM filtering that identifies malware and phishing attacks and has protocols against Ransomware.
See for yourself how easy email encryption can be with a free no-risk 14 day trial.
No comments:
Post a Comment